Kela Cyber
We Monitor, Hunt and Mitigate Cyber Crimes with Real Intelligence.
Automatically uncover your attack surface by leveraging attackers’ perspectives for proactive protection.
How Companies Use KELA
Case Management & Law Enforcement
Strengthen nation-state defenses. Access targeted, actionable intelligence for countering diverse cyber threats. Utilize rich on-premises data and expert insights to enhance efficiency, reduce false positives, and streamline threat profiling.
Cybercrime Attack Surface Visibility
Discover your attack surface from the attacker’s view. Analyze the adversary’s perspective of your company. This comprehensive understanding allows you to assess the level of risk your organization faces and to prioritize security measures accordingly.
Fraud Detection
Combat digital fraud involving online payments, refunds, bank cards, loyalty programs, and more. Use KELA’s technology and expert guidance for proactive defense against fraudulent schemes before they harm your organization.
Threat Intelligence
Anticipate potential threats by monitoring the behavior and activities of threat actors relevant to your industry or sector. Utilize KELA’s Threat Actors module for meticulous investigations of specific cyber criminals that extend to analyzing web signatures, handles, and other intricate details.
Third-party Intelligence
Use KELA’s automation to spot risks in your supply chain and attack surface. Get insights, monitor, prioritize high-risk vendors. Act: advise fixes or cut connections if needed.
Identity Theft Protection
Customize proactive protection against credential theft. Monitor and identify compromised accounts, including SAAS accounts. Utilize smart severity classification and seamlessly integrate with webhooks for swift responses.
Vulnerability Intelligence
Gather vulnerability intel: analyze bugs, monitor threats. Prioritize by impact. Use KELA for trending vulnerabilities, automate monitoring, spot network weaknesses, halt unauthorized access.
Brand Protection
Discover crucial insights about your brand from all over the cybercrime underground. Get a full view, act quickly. Strengthen your organization’s reputation and trustworthiness.
News
BẢO VỆ DỮ LIỆU VỚI PHẦN MỀM COMMVAULT
1. Ransomware Protection (bảo vệ khỏi phần mềm tống tiền) là gì? Ransomware Protection là quá trình ngăn chặn sự kiện cài đặt phần mềm
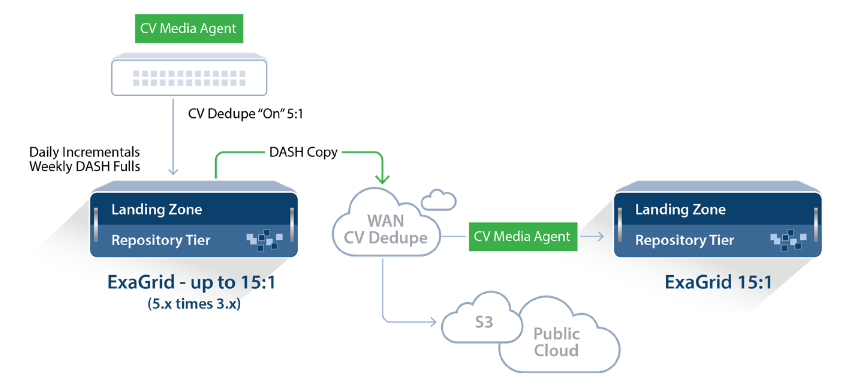
ExaGrid và Commvault: Chống trùng lặp tối đa và dễ dàng quản lý
1. Tóm tắt Báo cáo này ghi lại quá trình xác thực của Nhóm chiến lược doanh nghiệp của TechTarget đối với thử nghiệm ExaGrid,

Commvault được vinh danh là công ty dẫn đầu lần thứ 13 liên tiếp trong Gartner® Magic Quadrant năm 2024
Các nhà lãnh đạo I&O đang phải đối mặt với thách thức bảo vệ và khôi phục các ứng dụng và dữ liệu kinh doanh